### On-Demand Coupons
For immediate, manual distribution.
1. Navigate to your coupon-based instance.
2. Go to the **Coupons** tab and click **Generate Coupons**.
3. Specify the **Count** (how many to create, max 200 at a time) and how long they should be **Valid For**.
4. The generated codes will be displayed and can be distributed to guests.
### Scheduled Coupon Generation
For automated, recurring generation.
1. Navigate to your instance and go to the **Coupon Schedules** tab.
2. Click **Add Schedule**.
3. Configure the schedule to automatically generate a batch of coupons on a `Daily`, `Weekly`, or `Monthly` basis (e.g., "Generate 50 new 8-hour coupons every day at 8 AM").
4. Select a **Notification Group** to receive an email with a link to the generated coupons.
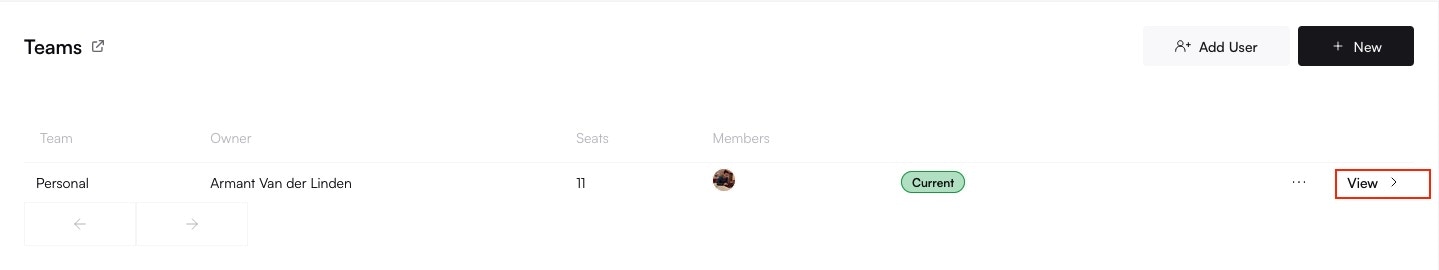
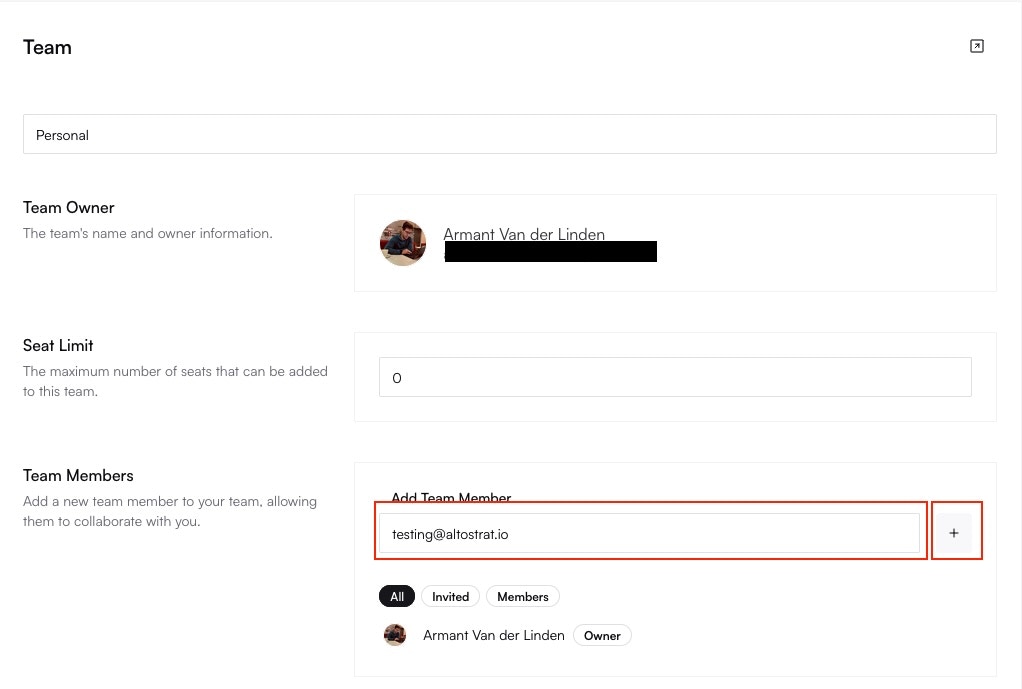
## Part 4: Monitoring and User Management
From the main site overview page, navigate to the **Captive Portal Users** tab to see a list of all users who are currently active or have previously connected through the portal at that site. From here, you can:
* View session details like IP address, MAC address, and session expiration.
* Manually disconnect an active user session if needed.
# Introduction to Captive Portals
Source: https://altostrat.io/docs/sdx/en/connectivity/captive-portals/introduction
Understand how to create branded, secure guest Wi-Fi experiences with Altostrat's Captive Portal service, using OAuth2 or coupon-based authentication.
Altostrat's Captive Portal service allows you to provide secure, controlled, and branded internet access for guests on your network. When a user connects to a designated guest Wi-Fi or LAN segment, their traffic is intercepted and they are redirected to a customizable login page. They must authenticate before gaining full internet access.
This is ideal for corporate guest networks, retail locations, hotels, and any environment where you need to manage and track guest access.
## How It Works: The Connection Flow
The magic of the captive portal happens through a seamless, automated redirection process. When a guest's device tries to access the internet, your MikroTik router intelligently intercepts the request and guides them through authentication.
```mermaid theme={null}
graph TD
subgraph "Guest's Device"
A[1\. Connects to Wi-Fi




 ### How to Restore a Configuration
Restoring a configuration allows you to revert a device to a previously known-good state. This is a manual, multi-step process designed for safety.
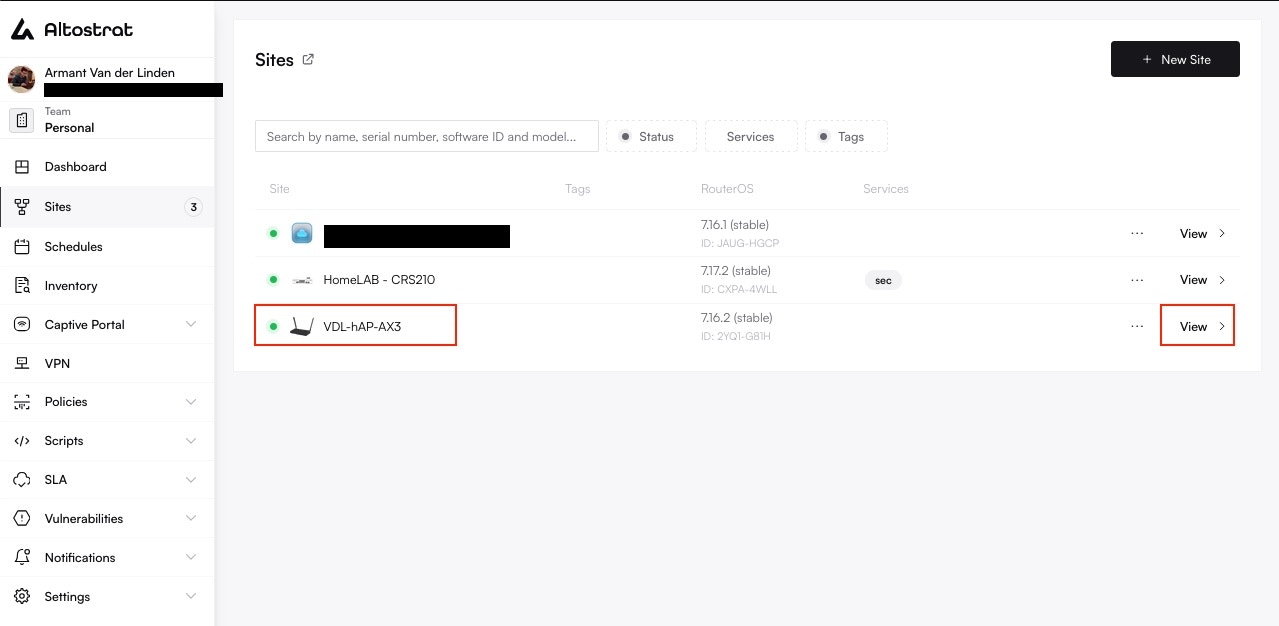
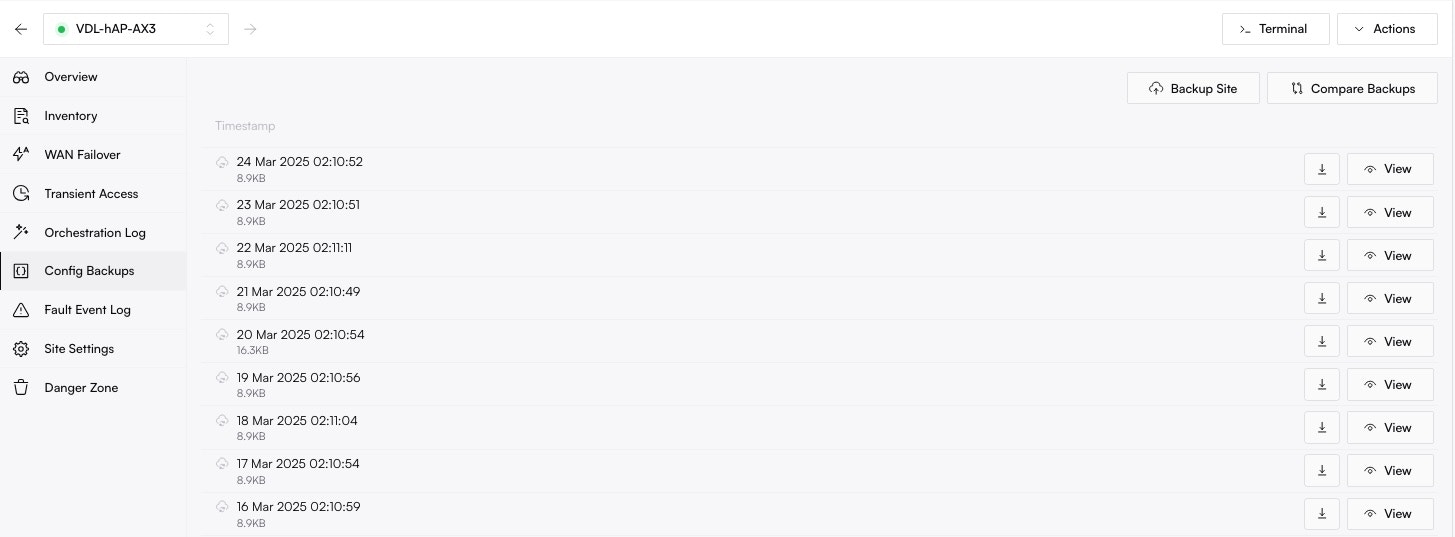
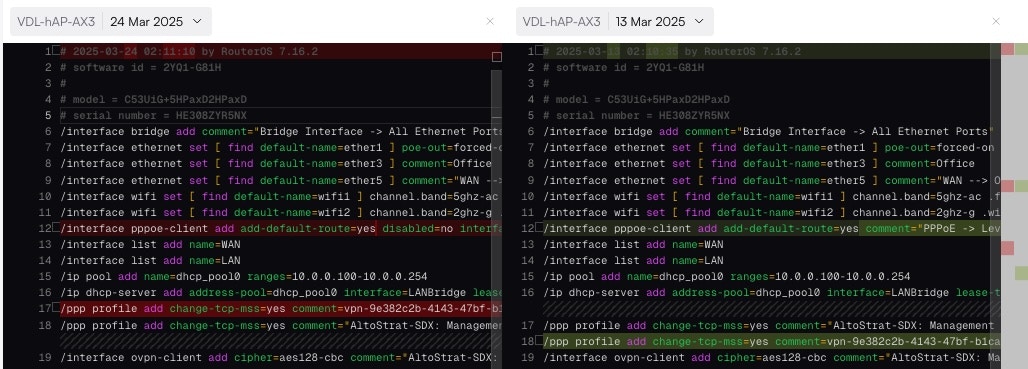
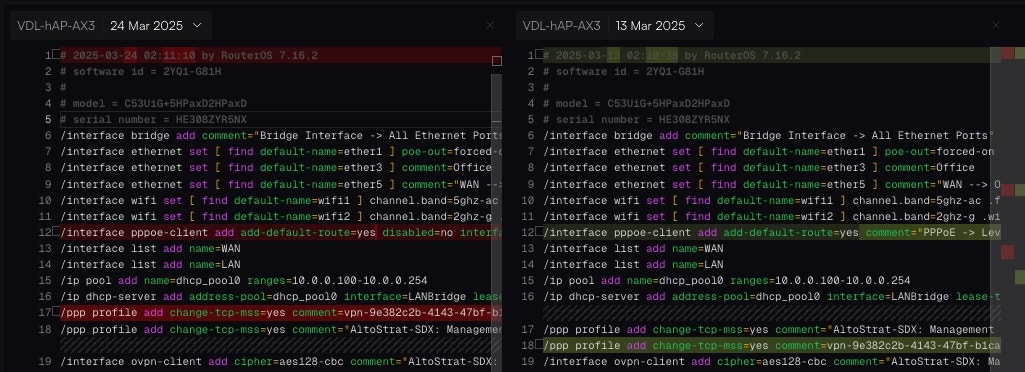
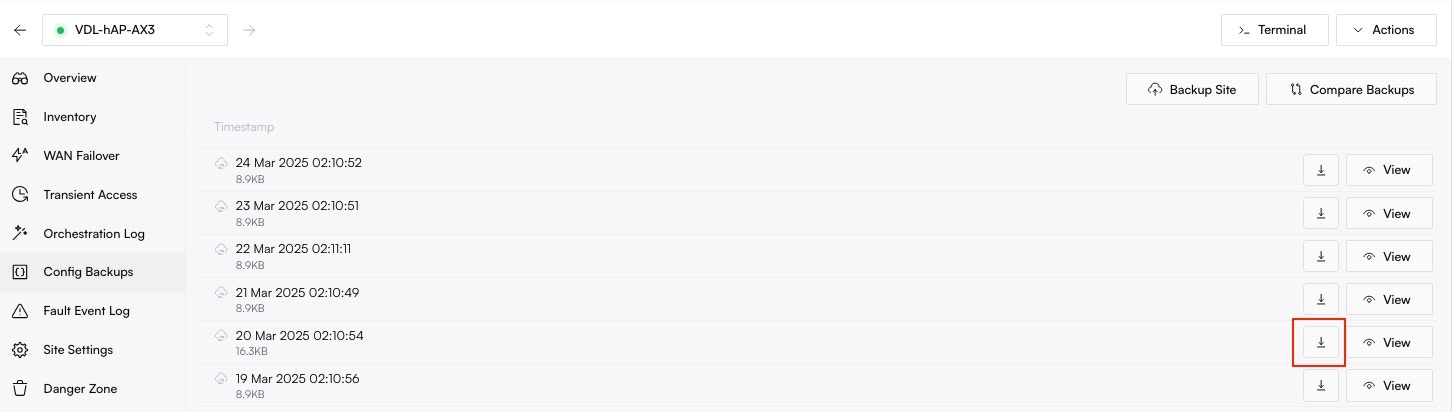
### How to Restore a Configuration
Restoring a configuration allows you to revert a device to a previously known-good state. This is a manual, multi-step process designed for safety.
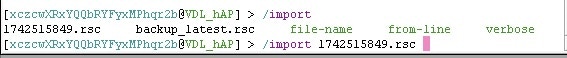 The router will execute the script, apply the configuration, and likely reboot. Once it comes back online, it will be running the restored configuration.
The router will execute the script, apply the configuration, and likely reboot. Once it comes back online, it will be running the restored configuration.
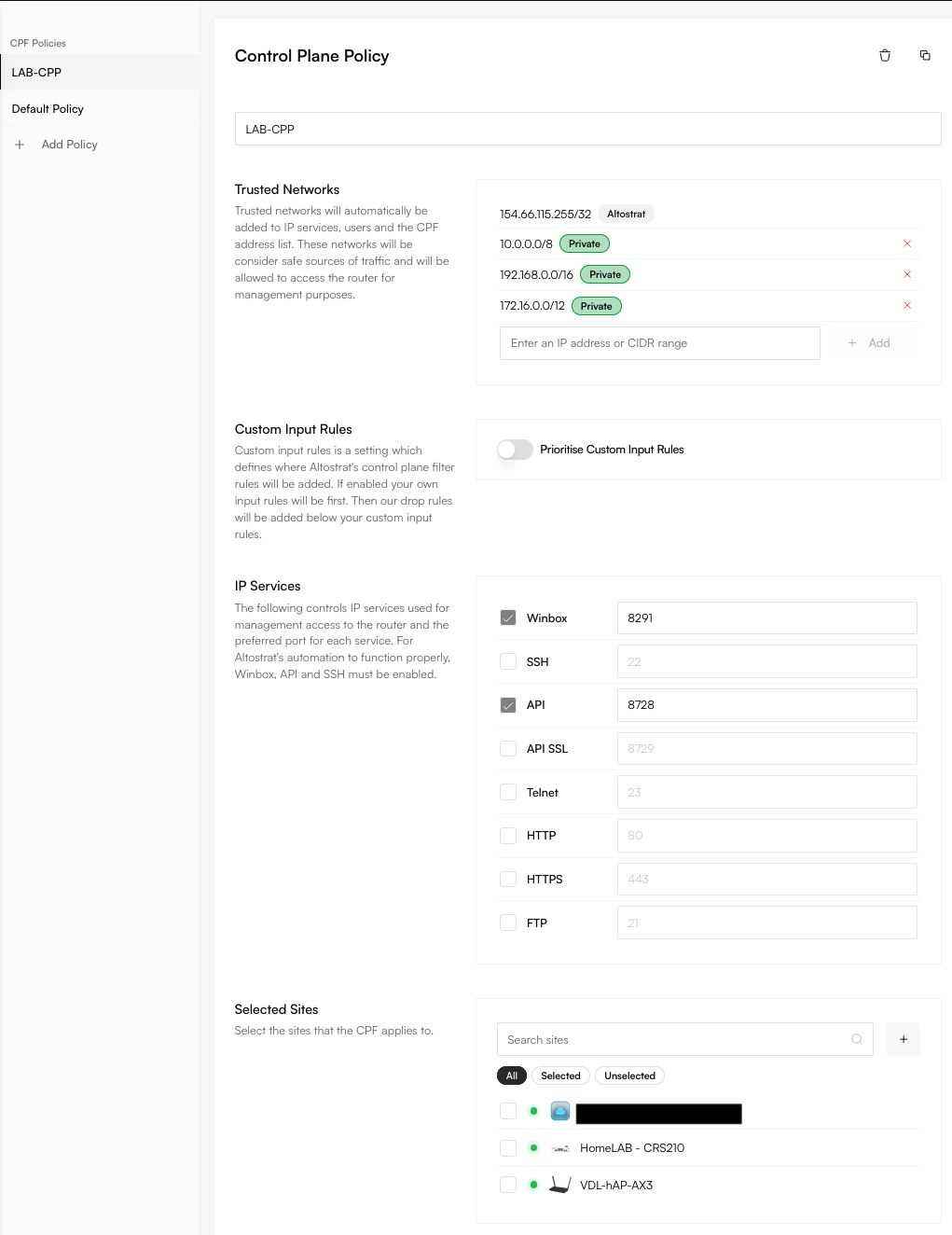
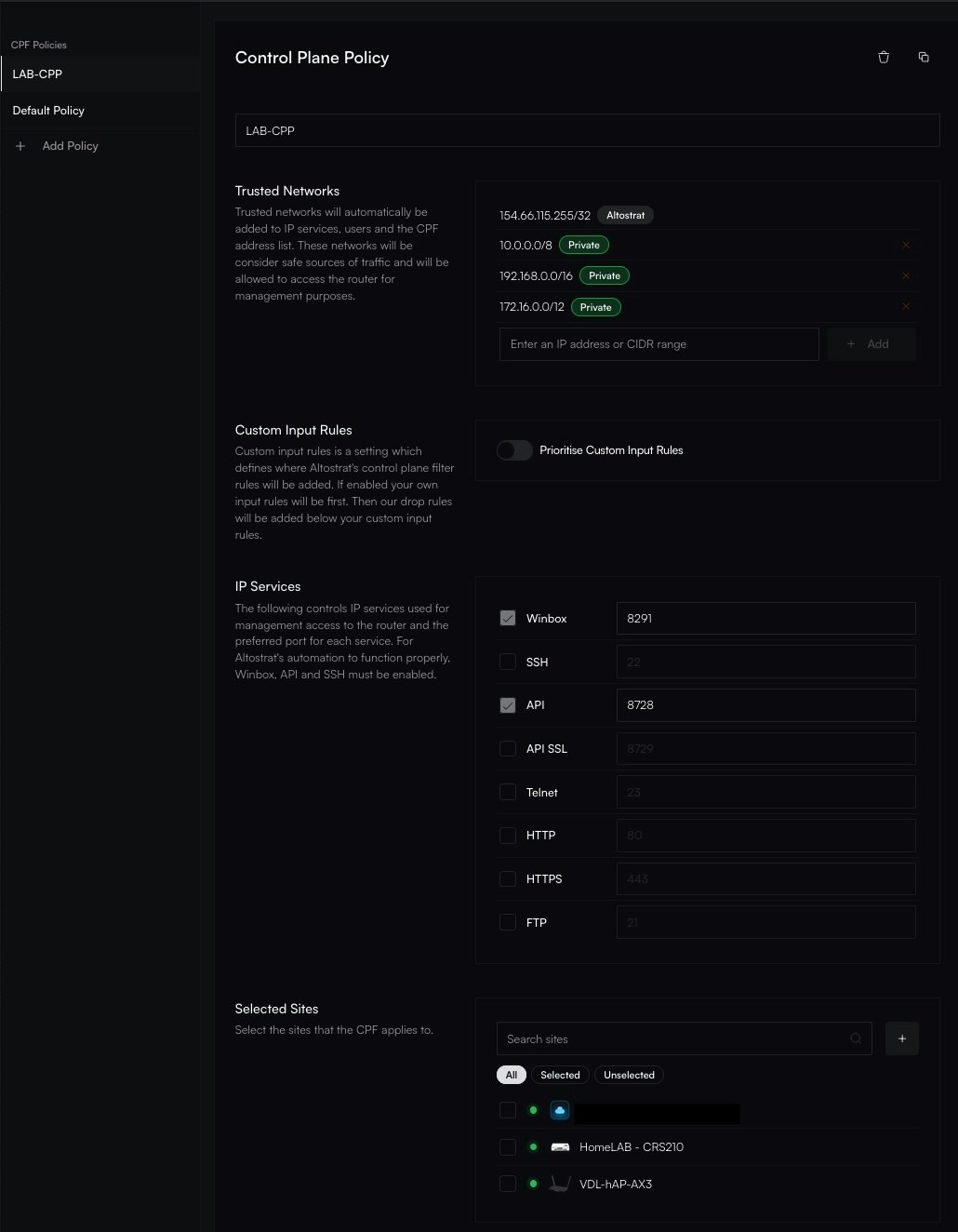
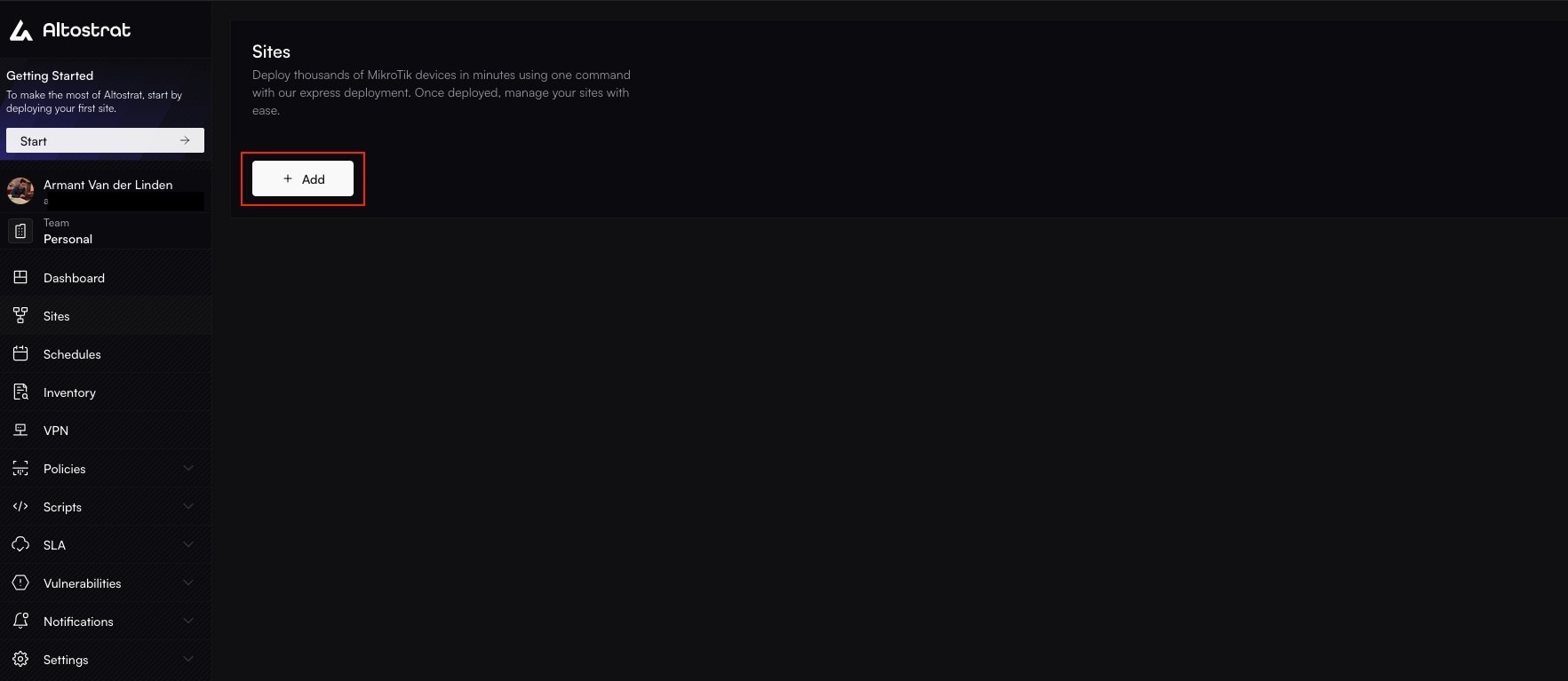
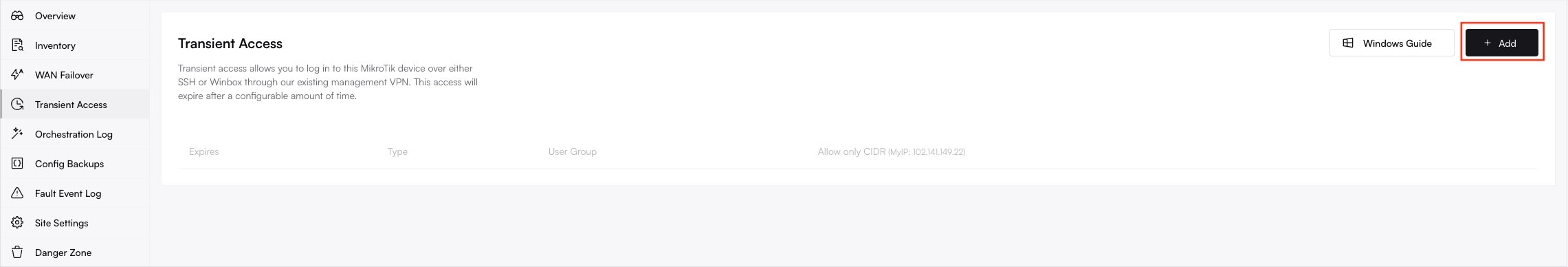
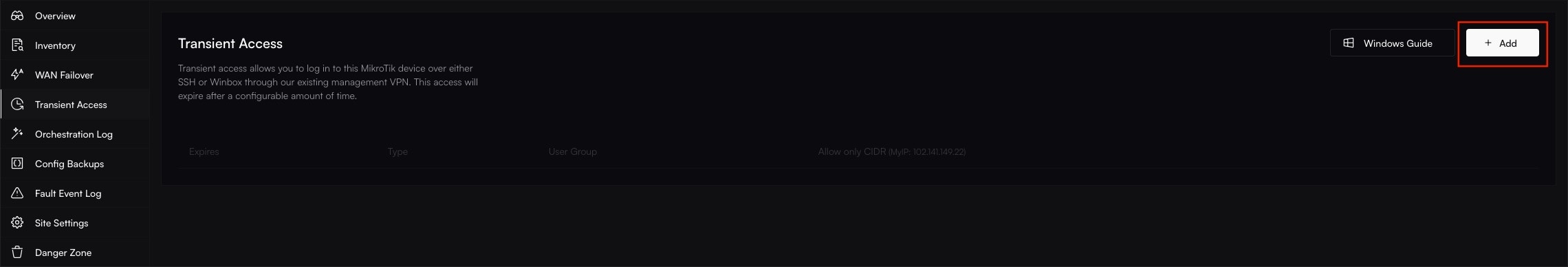
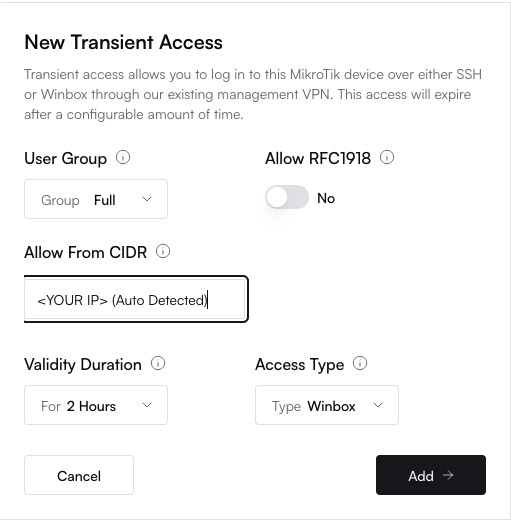
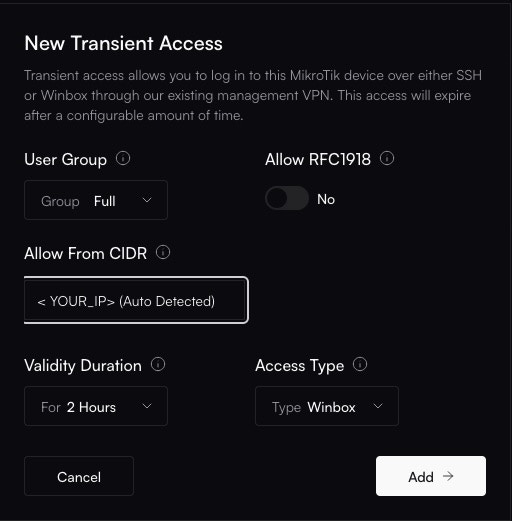
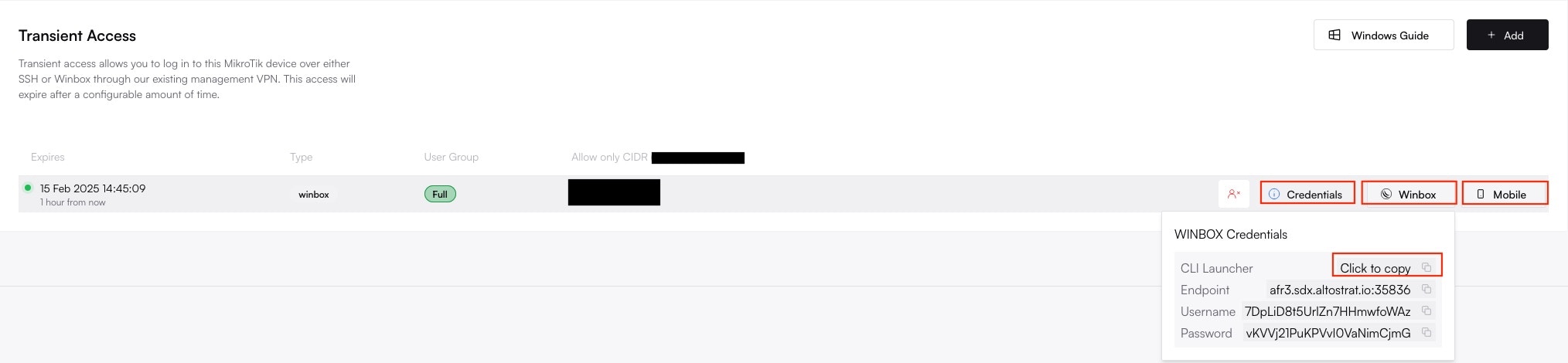
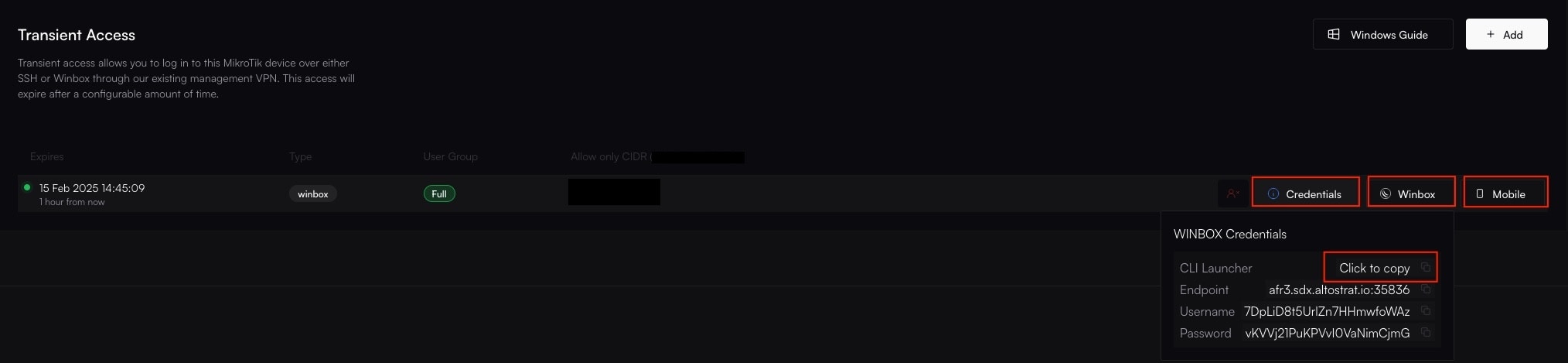



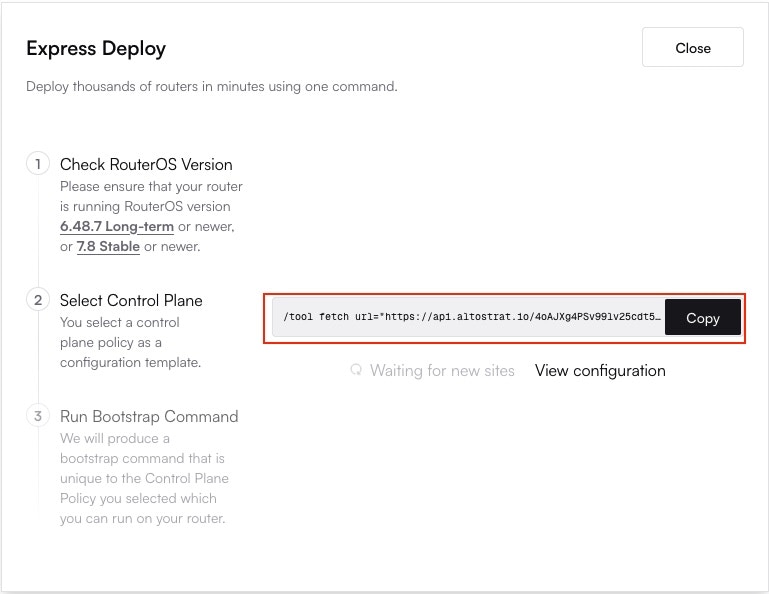
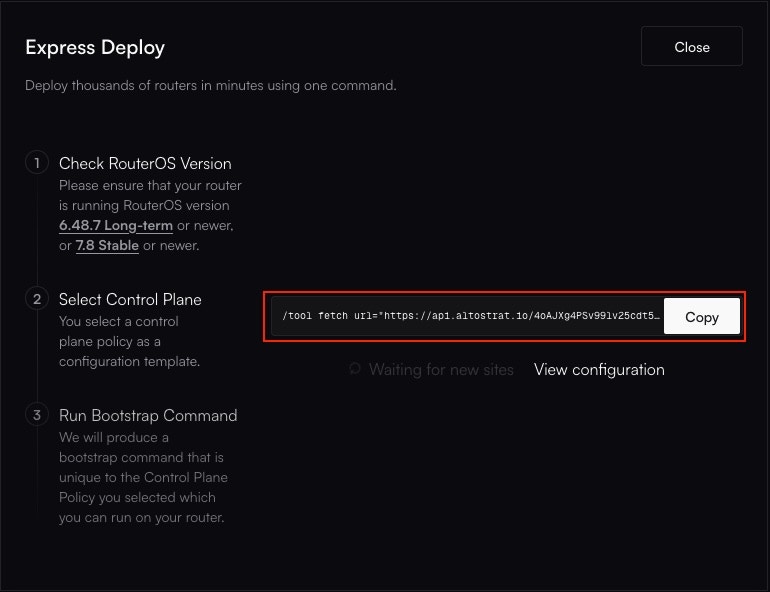
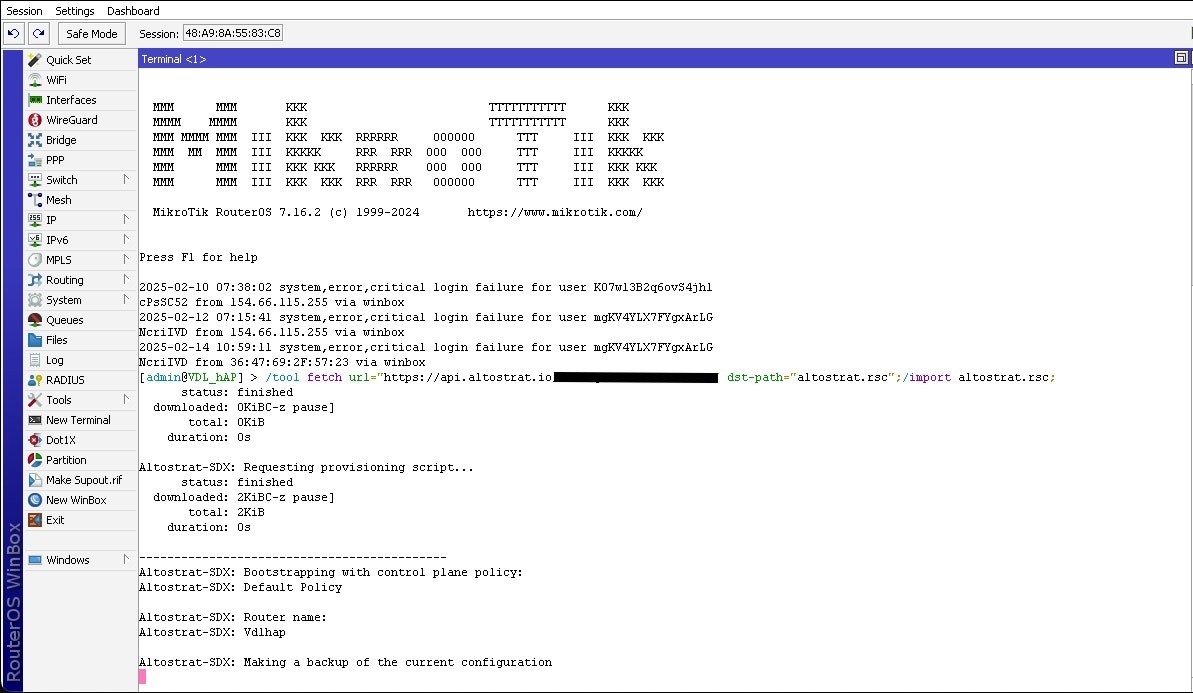
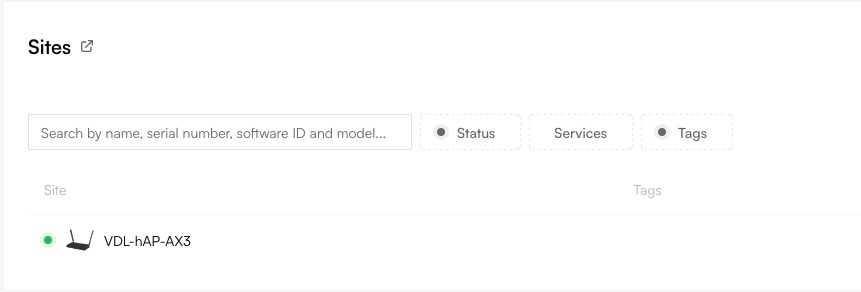
 **Congratulations!** Your MikroTik router is now fully onboarded and managed by Altostrat SDX.
**Congratulations!** Your MikroTik router is now fully onboarded and managed by Altostrat SDX.
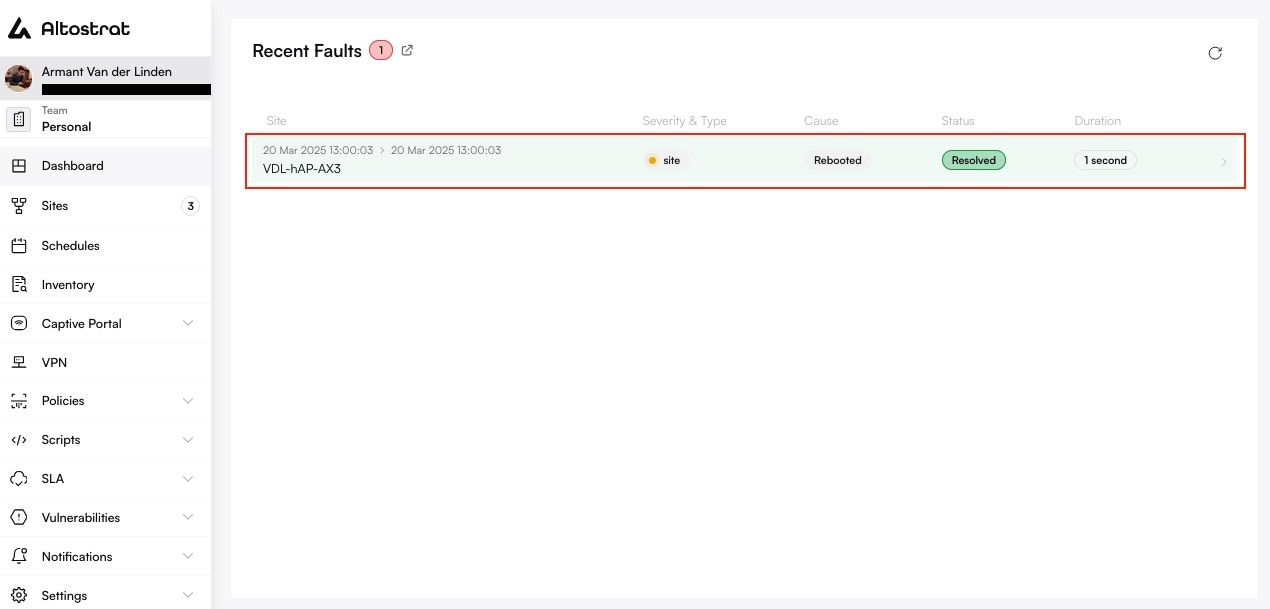
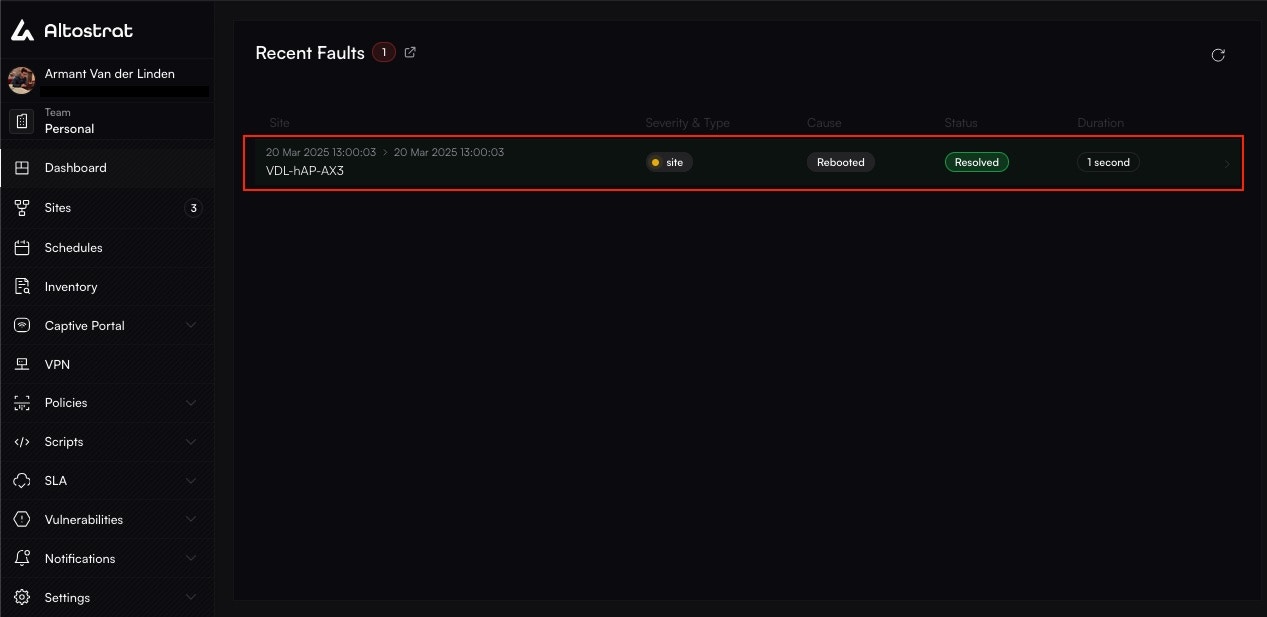 ### The Site-Specific Fault Log
For a complete history, navigate to a specific site and click on the **Faults** tab. This provides a detailed, filterable log of every incident that has ever occurred for that site and its associated resources (like its WAN links).
### The Site-Specific Fault Log
For a complete history, navigate to a specific site and click on the **Faults** tab. This provides a detailed, filterable log of every incident that has ever occurred for that site and its associated resources (like its WAN links).
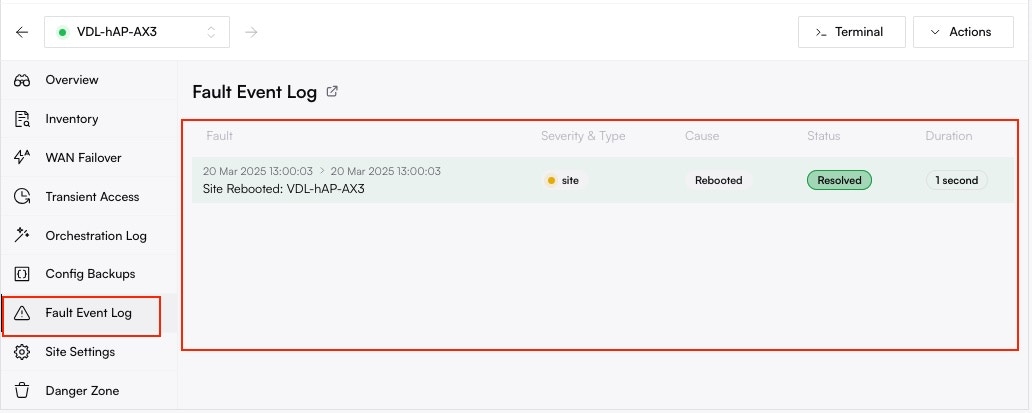
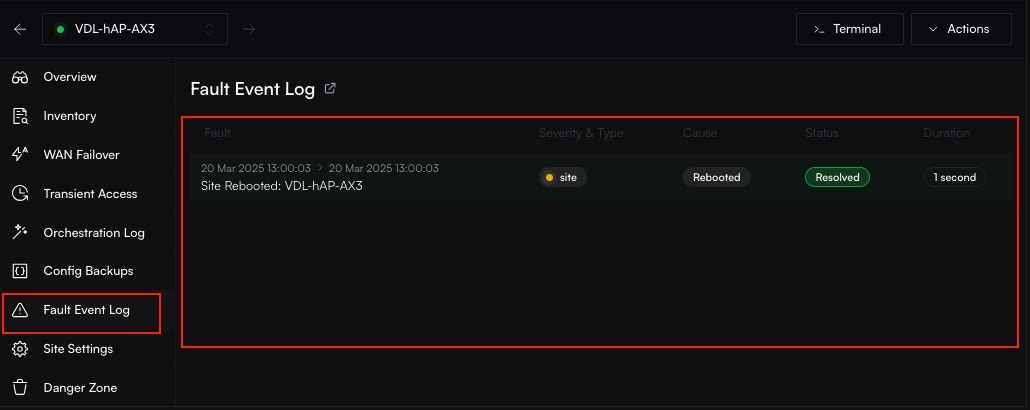 ## Filtering to Find Answers
Use the powerful filter controls at the top of the Fault Log to answer specific troubleshooting questions.
## Filtering to Find Answers
Use the powerful filter controls at the top of the Fault Log to answer specific troubleshooting questions.
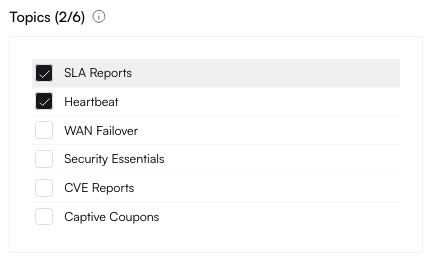
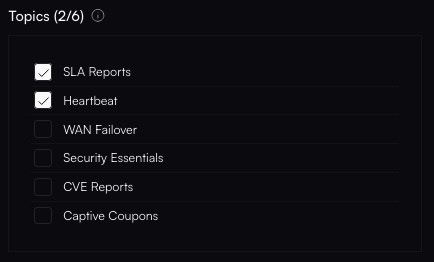
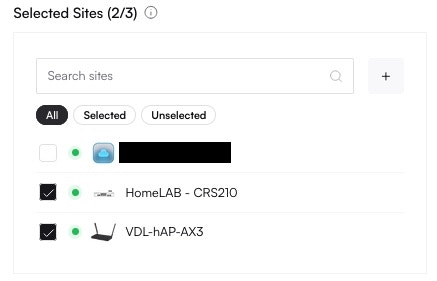
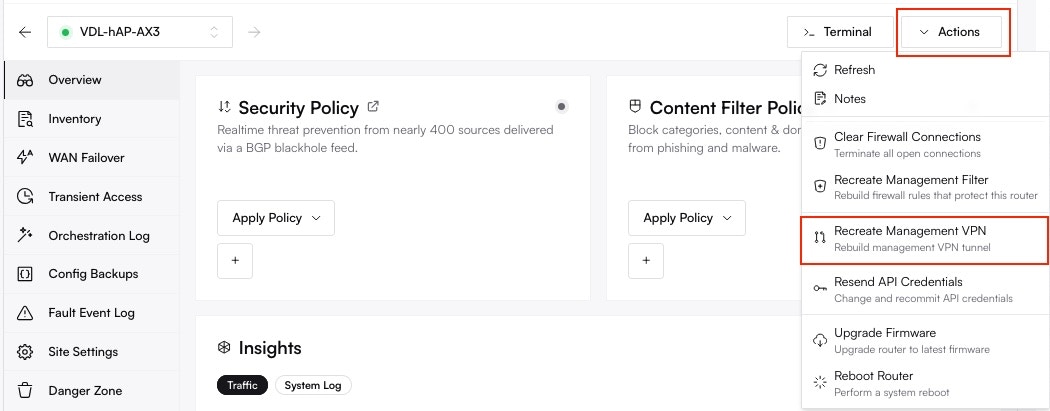
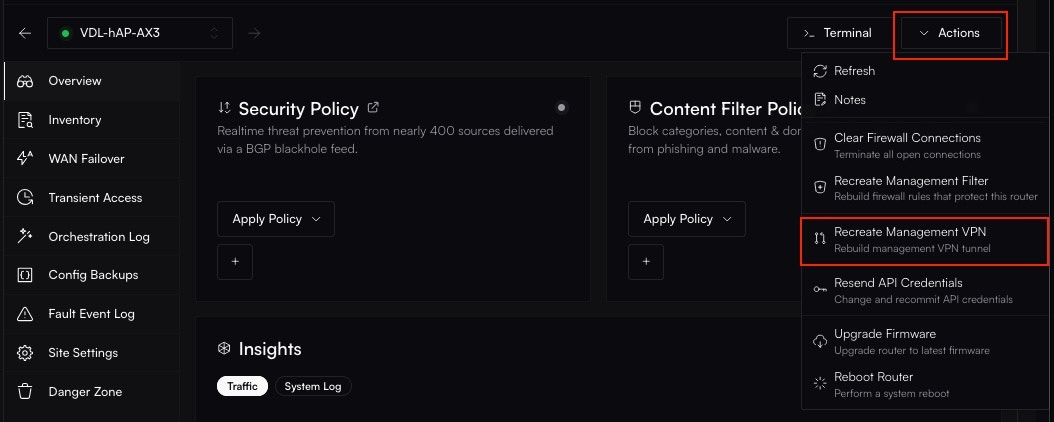
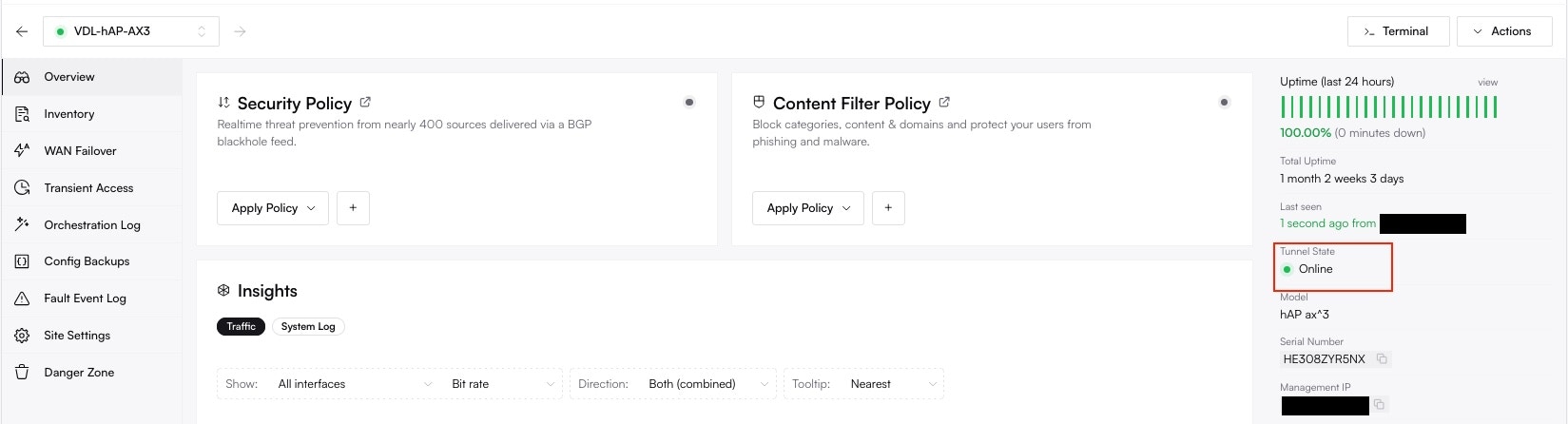
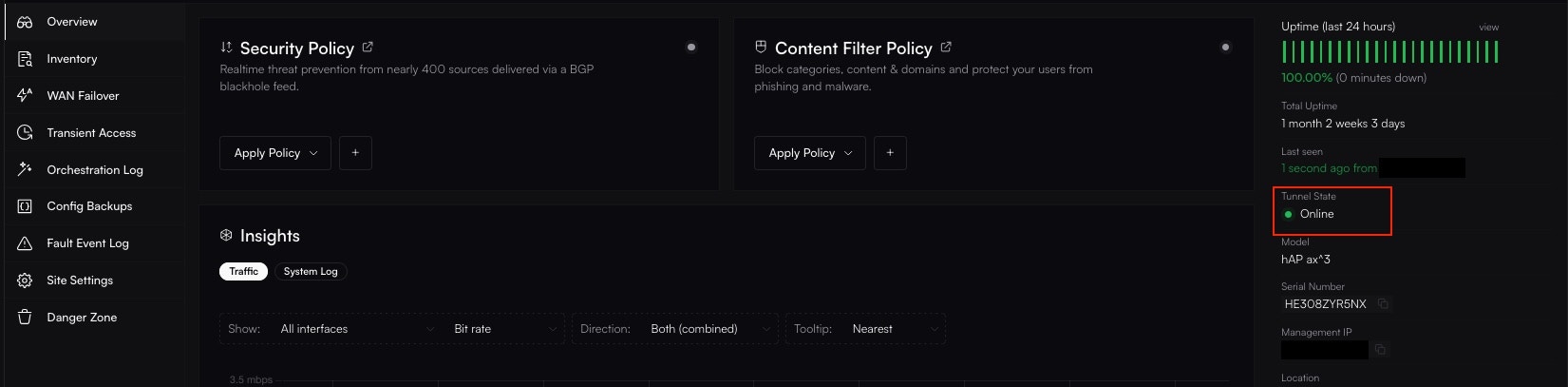
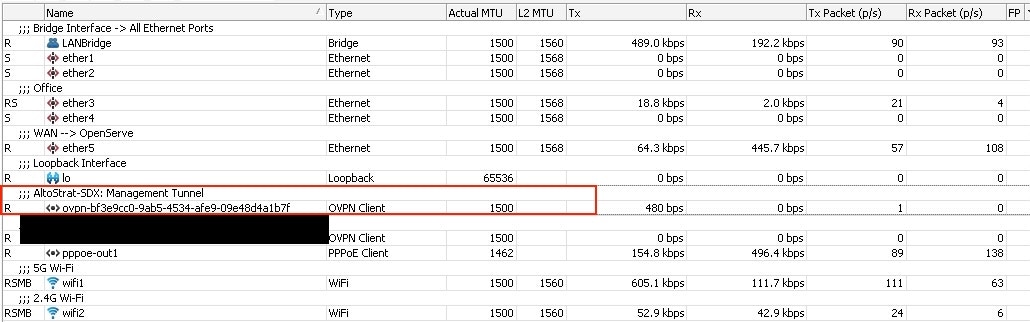
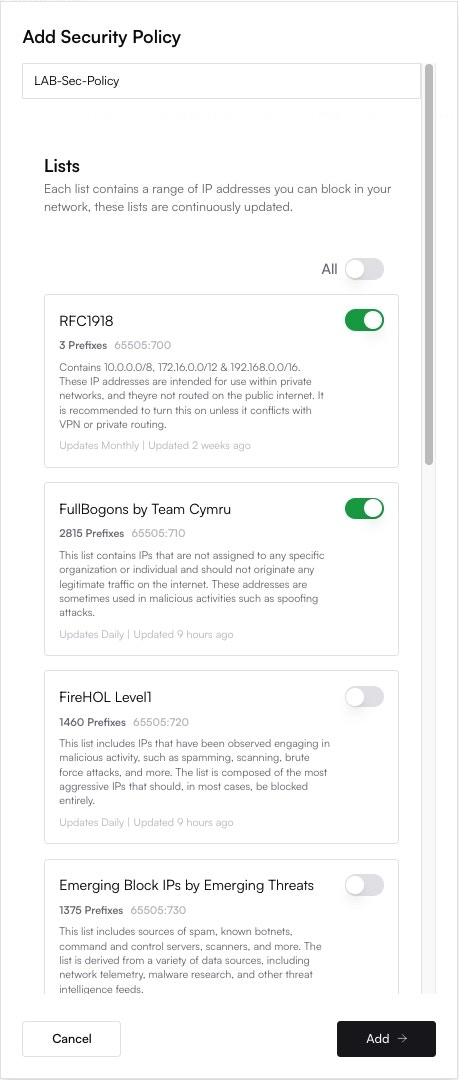
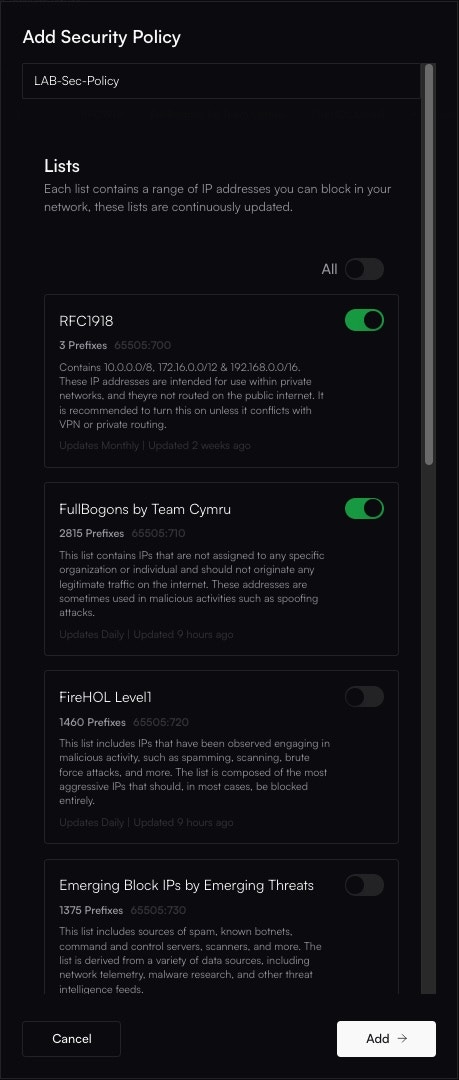
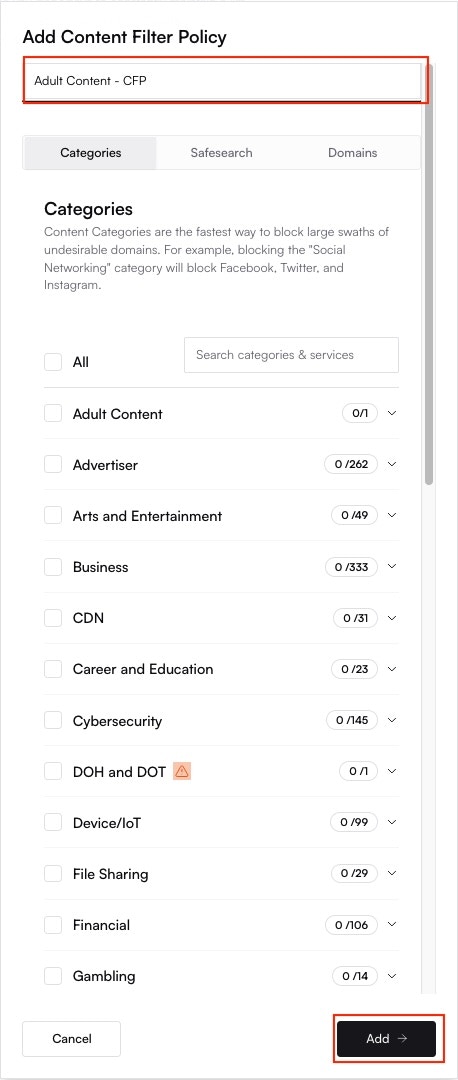
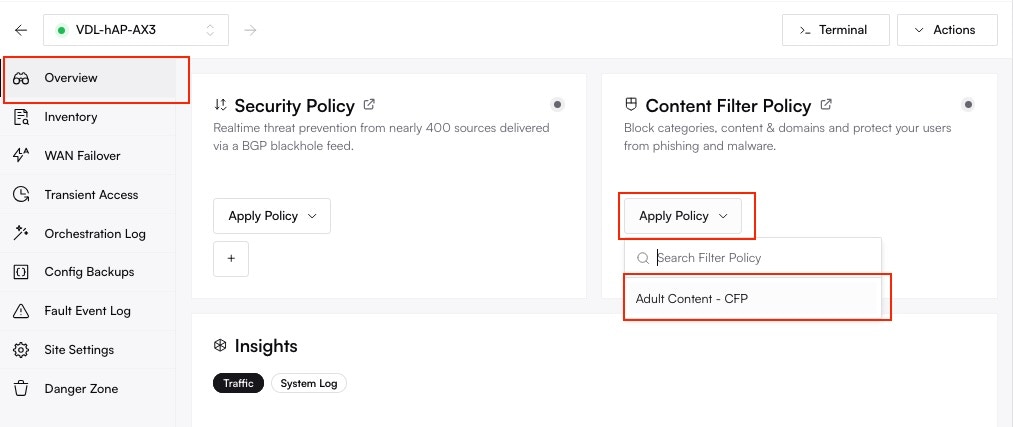
 Altostrat will now orchestrate the necessary changes on the device. Allow a few moments for the policy to take effect.
## Managing Existing Policies
To edit or delete a policy, navigate back to **Policies → Content Filtering**.
* **To Edit:** Click on the policy name, make your changes, and save. The updates will automatically apply to all assigned sites.
* **To Delete:** Click the trash can icon next to the policy.
Altostrat will now orchestrate the necessary changes on the device. Allow a few moments for the policy to take effect.
## Managing Existing Policies
To edit or delete a policy, navigate back to **Policies → Content Filtering**.
* **To Edit:** Click on the policy name, make your changes, and save. The updates will automatically apply to all assigned sites.
* **To Delete:** Click the trash can icon next to the policy.